As mobile operators migrate from legacy EPC-based architectures to full 5G Standalone (SA), one of the most fundamental transformations occurs in the security model.
While many assume that 5G security is simply “4G with stronger encryption,” the reality is far more significant.
5G introduces new architectural principles, new attack surfaces, and new mechanisms specifically engineered to address long-standing vulnerabilities in previous generations.
This article explains the three core security changes that distinguish 5G from 4G — and why they matter for operators preparing for 5G-Advanced and 6G.
1. SUPI Encryption: Protecting Subscriber Identity by Design
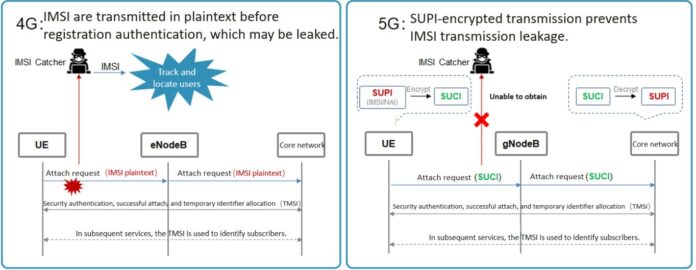
One of the most critical weaknesses in 2G, 3G, and even 4G was how the IMSI (International Mobile Subscriber Identity) could occasionally be transmitted in cleartext over the air.
This exposed subscribers to:
-
IMSI-catchers
-
identity tracking
-
location monitoring
-
impersonation attacks
5G eliminates this vulnerability through the concept of SUPI encryption.
How it works
The subscriber identity (SUPI) is encrypted into a SUCI using the Home Network’s public key, which is securely stored in the USIM.
This ensures:
-
identity protection before authentication
-
resistance against passive and active interception
-
improved privacy for all 5G devices, including IoT and enterprise terminals
This change alone represents one of the most impactful improvements in mobile network security.
2. Integrity Protection on the User Plane
In LTE, user-plane integrity protection was optional and rarely implemented due to performance overhead.
In 5G Standalone, integrity protection becomes a native capability and a key part of the overall threat model.
Why integrity protection matters
User-plane integrity protection allows the network to verify that user data has not been:
-
modified
-
injected
-
replayed
-
corrupted
This is especially important for:
-
URLLC applications
-
autonomous systems
-
critical IoT
-
enterprise and industrial 5G deployments
As 5G networks evolve, the requirement for tamper-resistant data flows becomes essential for mission-critical use cases.
3. API Security and Network Exposure in the 5G Core
The move from EPC to 5G Core (5GC) introduces a paradigm shift:
Service-Based Architecture (SBA).
Instead of relying on Diameter interfaces, the 5G Core exposes network functions as APIs via:
-
HTTP/2
-
TLS encryption
-
OAuth2-based authorization
This modern, cloud-native design introduces flexibility but also creates new security challenges.
Key risks
-
API abuse
-
improper exposure of network capabilities
-
credential or token compromise
-
lack of access control granularity
Key requirements for operators
To mitigate these risks, operators must implement:
-
Zero-Trust Architecture
-
API governance frameworks
-
mutual authentication between network functions
-
continuous authorization and token validation
-
strong encryption across all interfaces
In practice, this means that every API call in the core network must be authenticated, authorized, and monitored.
4. Why Zero-Trust Becomes Mandatory in 5G SA
In traditional mobile core networks, security was based on a perimeter-trust model.
In 5G SA, that model is no longer viable.
Because the 5G Core is cloud-native, distributed, and API-driven, the network must assume:
“An attacker may already be inside the system.”
Zero-trust principles therefore become essential:
-
never trust by default
-
always authenticate
-
always authorize
-
continuously verify the integrity and legitimacy of each request
As 5G networks incorporate edge computing, network slicing, and exposed service interfaces, zero-trust evolves from a best practice into a critical requirement.
Conclusion: Preparing for 5G-Advanced and 6G
The shift from 4G to 5G is not only about enhanced performance — it represents a complete rethinking of the security architecture of mobile networks.
Identity protection, integrity verification, and API-centric security become foundational pillars that operators must master to ensure safe, scalable deployments.
Operators that invest early in these capabilities will be better positioned for the transition to:
-
5G-Advanced
-
6G security frameworks
-
mass IoT deployments
-
network slicing commercialization
Security in 5G is not an add-on.
It is a built-in design principle, and it will define the robustness of next-generation networks.
Learn More About 5G Technologies
Explore the full 5GWorldPro recorded training catalog to deepen your expertise in 5G Core, RAN, security, slicing, and 5G-Advanced evolution.
Benefit from Massive discount on our 5G Training with 5WorldPro.com
Start your 5G journey and obtain 5G certification
contact us: contact@5GWorldPro.com